2023-春秋杯pwn-wp
本文最后更新于:2023年5月27日 凌晨
2023-春秋杯pwn-wp
一共六道题,比赛期间做出来4道,排名92。
babyaul那道题纯属不太会,three-boy那道题主要是最后一天排名落后了,就不太想做了。
p2048
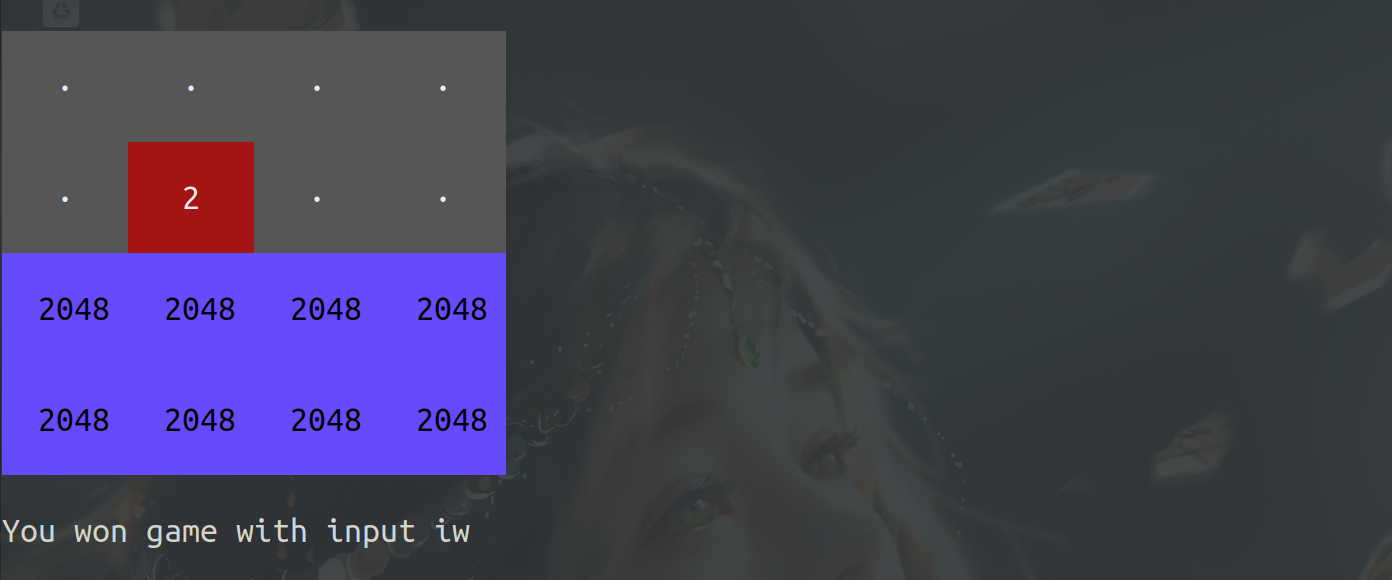
题目是一个小游戏,有点怪怪的。玩通关即可获取shell。
easy_LzhiFTP_CHELL
查看保护。
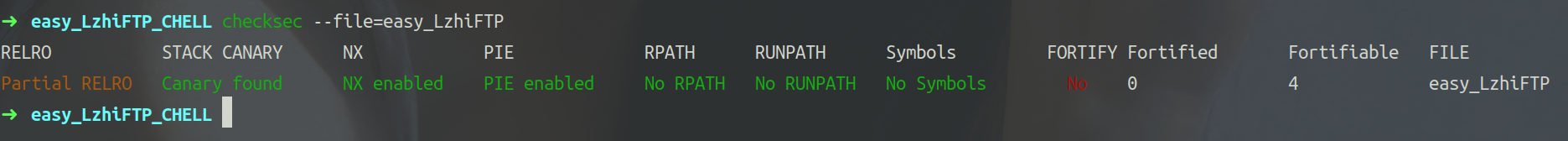
程序设置伪随机数作为登录密码。
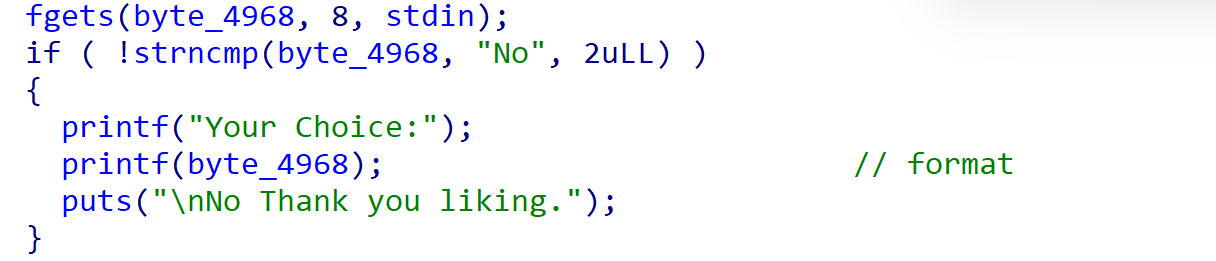
程序存在格式化字符串漏洞,可以泄露程序基地址。
程序分配时,多分配一次造成溢出。
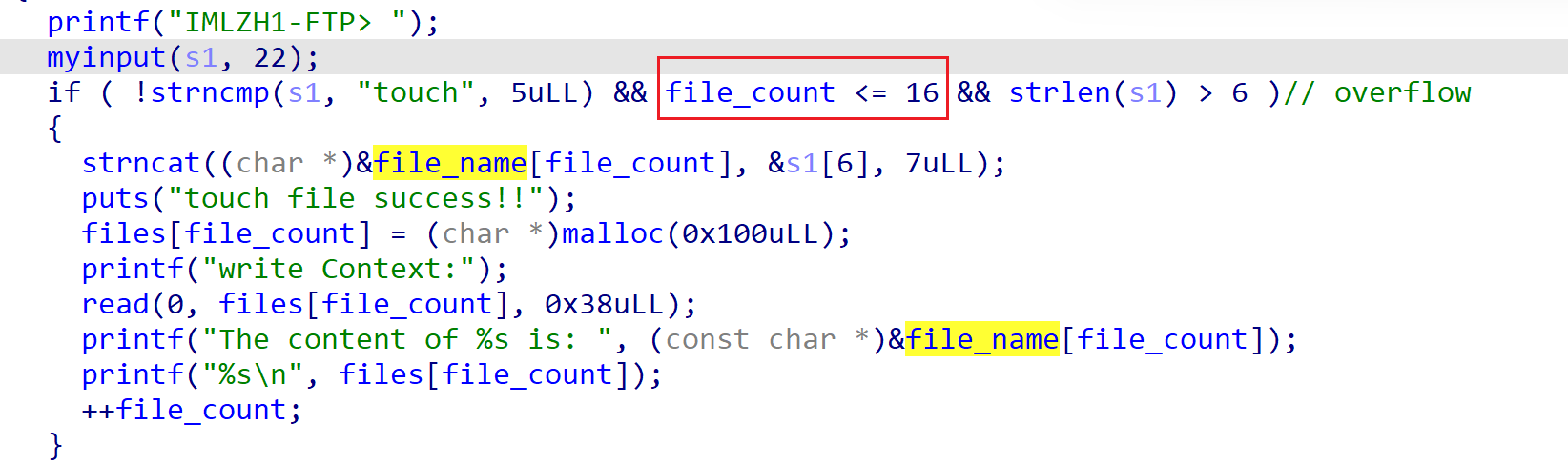
覆盖free的got表为system_plt。
1 | |
babygame
检查保护。
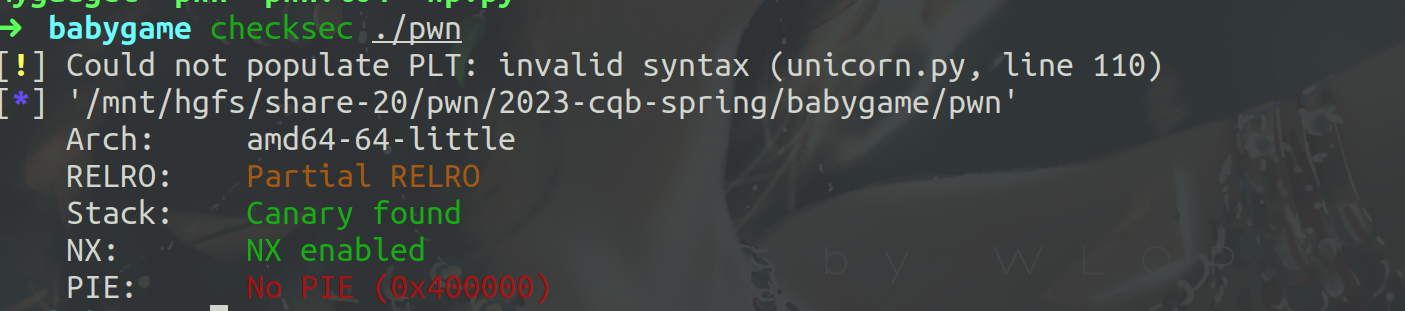
分配一段可读可写可执行的地址。
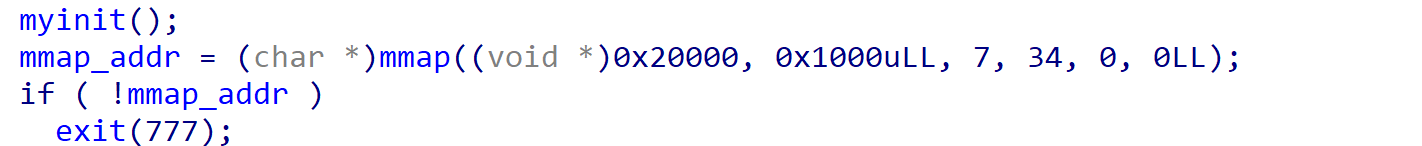
玩游戏刷钱。也就是1~4位md5值爆破。
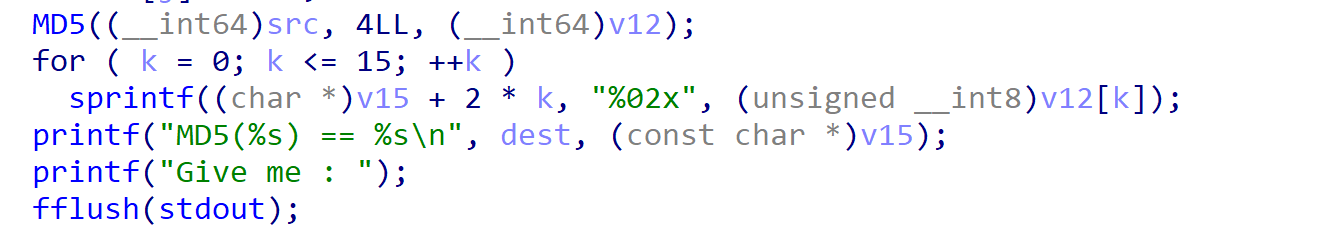
1 | |
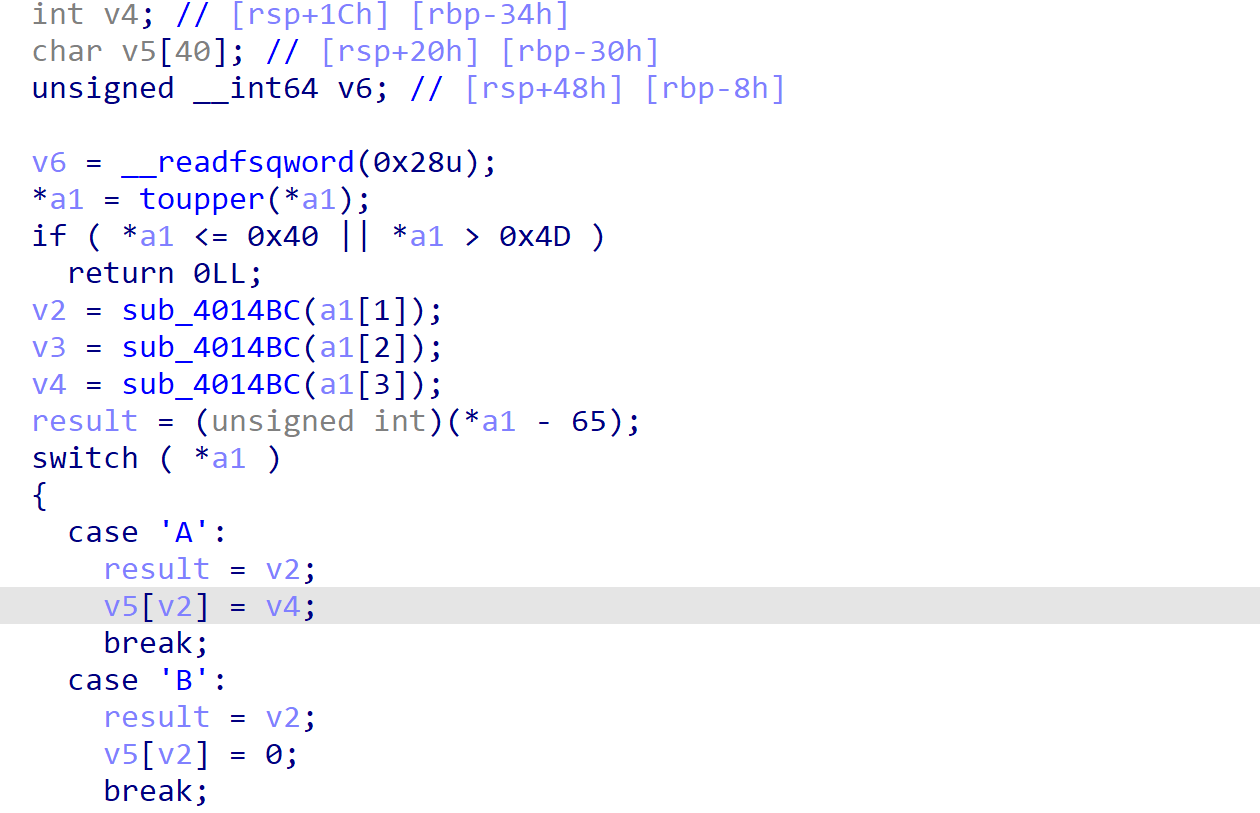
得到足够的钱后,调用sub_401396获取足够的执行次数,调用sub_40124D将数据写入mmap分配的空间,最后调用sub_401072执行vm指令。
其中,实现vm虚拟指令部分存在数组溢出。可以覆盖返回地址为mmap,从而执行可见字符shellcode。
1 | |
sigin_shellcode
查看保护。
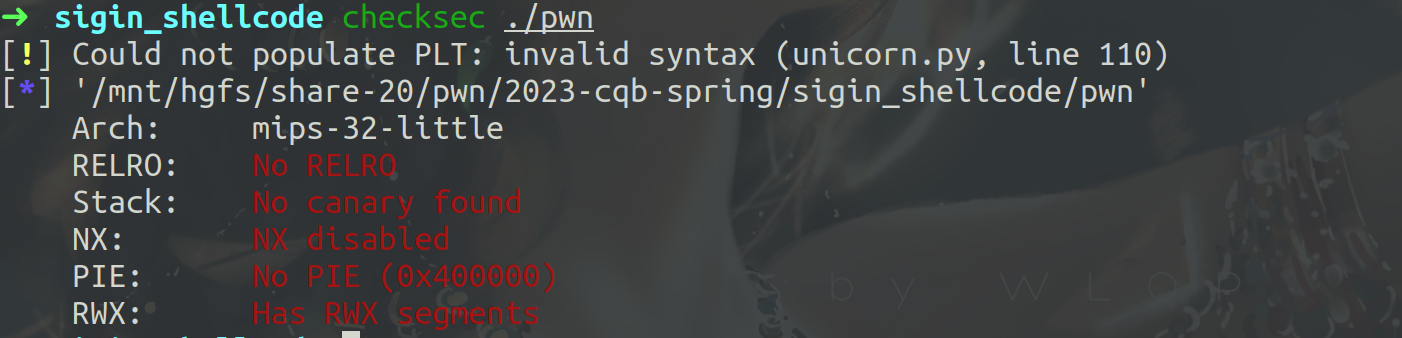
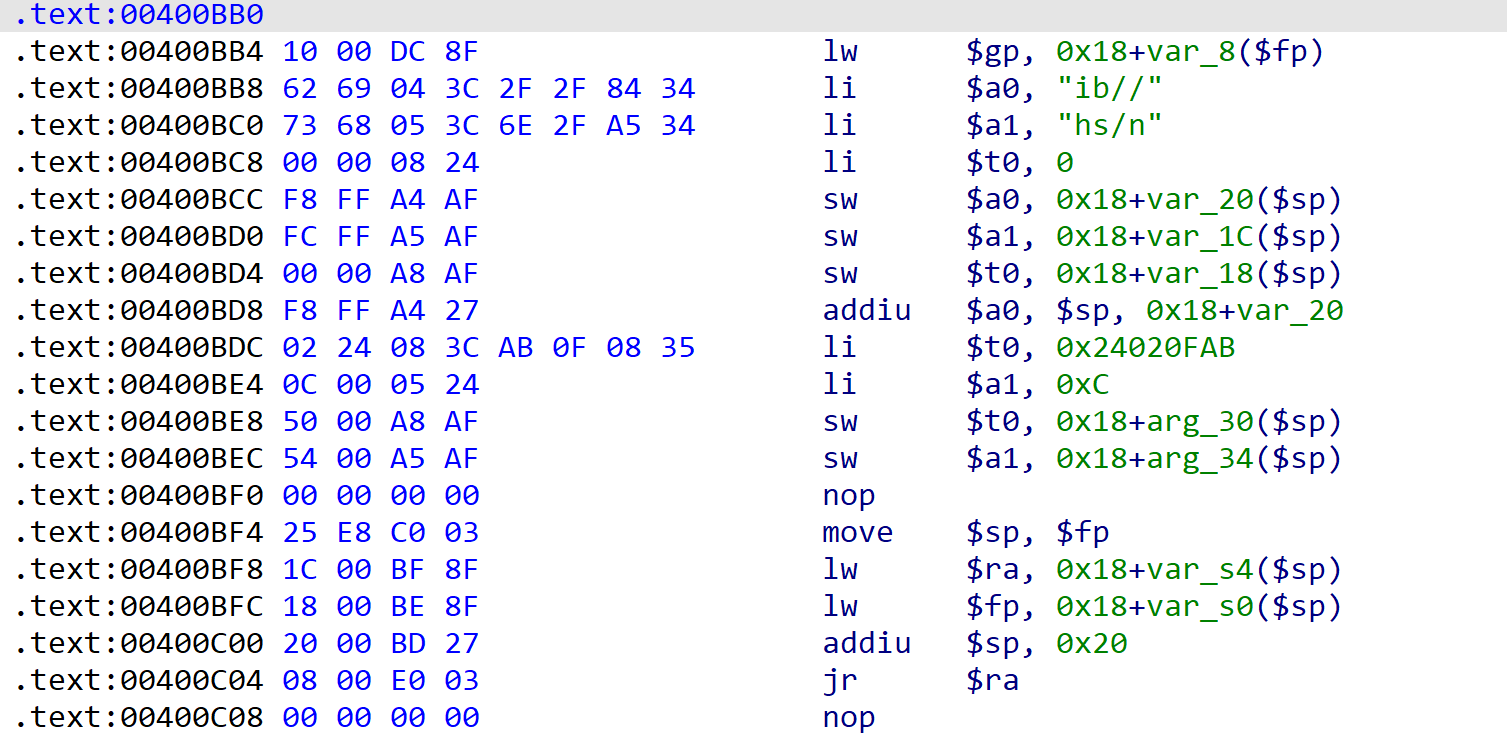
mips32架构下的pwn题。
伪随机数,下到100层获取足够的钱。
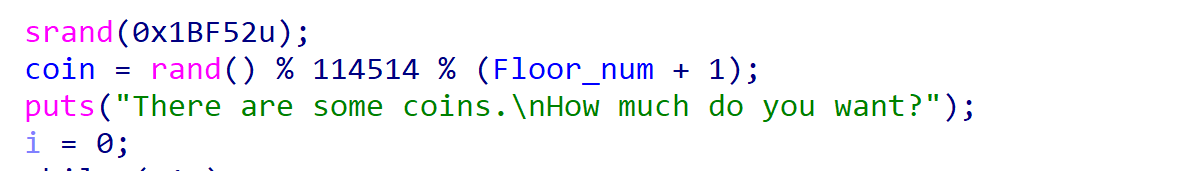

通过获得的钱购买战斗力。
最后战斗,战胜boss后,获取执行shellcode的机会。
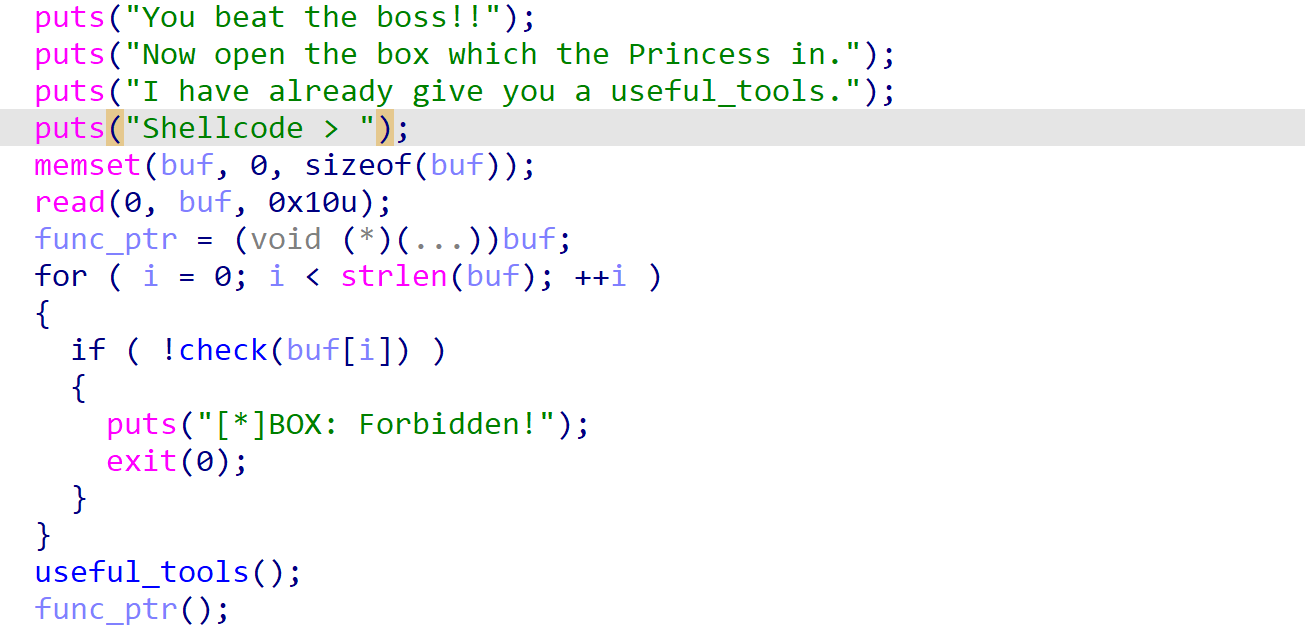
shellcode要求是mips32架构下的可见字符,题目已经给了大部分shellcode,我们只需要使execve第2个与第3个参数为0即可,即使$a1, $a2为0。
1 | |
至于随机数,笔者利用题目给的libc库总是失败。也没想到其他办法,笔者这里的思路是爆破。
1 | |
将每次爆破的值存储到文件中,最后读取文件即可获取rand值。
1 | |
爆了大概10分钟左右吧,就把所有的随机数都爆出来了。
babyaul
c语言与lua脚本的结合。
查看保护
我们的程序一开始是无法运行的,题目修改了lua脚本的文件头,我们复原文件头即可。
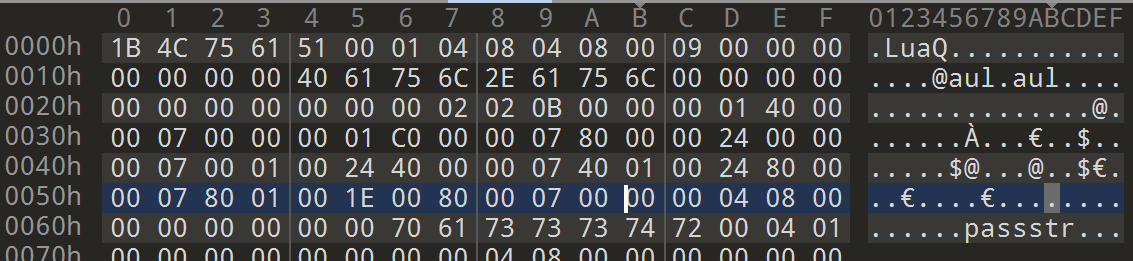
即把Aul修改为Lua。
我们使用unlua反编译bins,得到lua脚本。
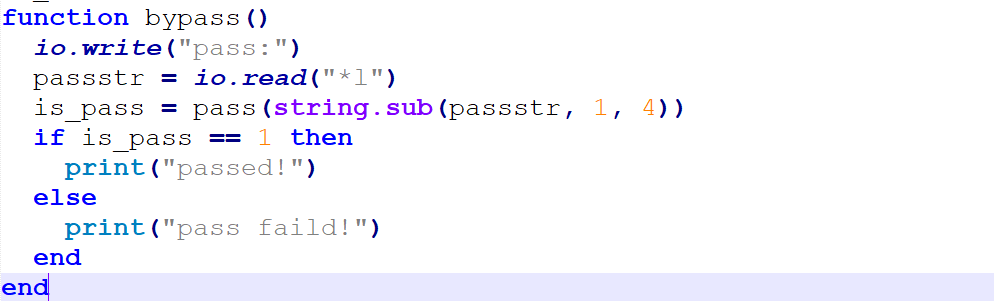

lua调用c语言pass对字符进行加密,通过后即为我们熟悉的菜单堆。
我们通过对babyaul进行逆向找到pass加密逻辑。
程序优先加载bins文件,这也就是我们一开始运行失败的主要原因。
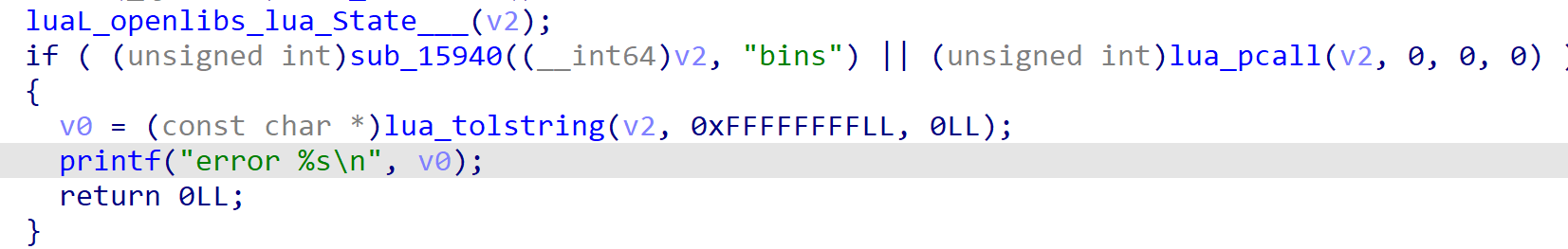
pass加密逻辑为随机输入4个一定范围的字符,然后进行sha256加密。
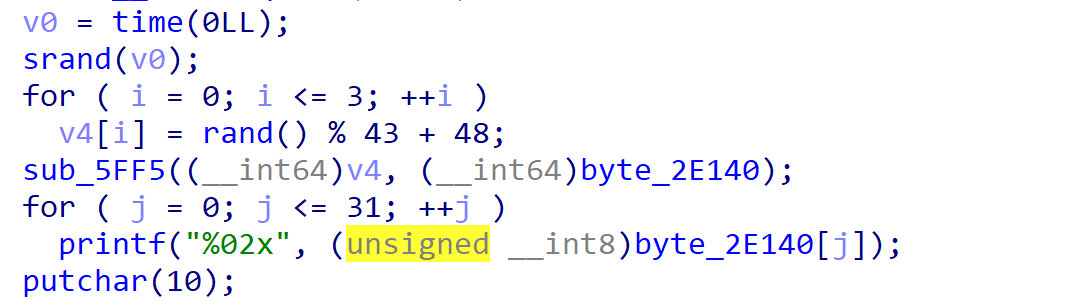
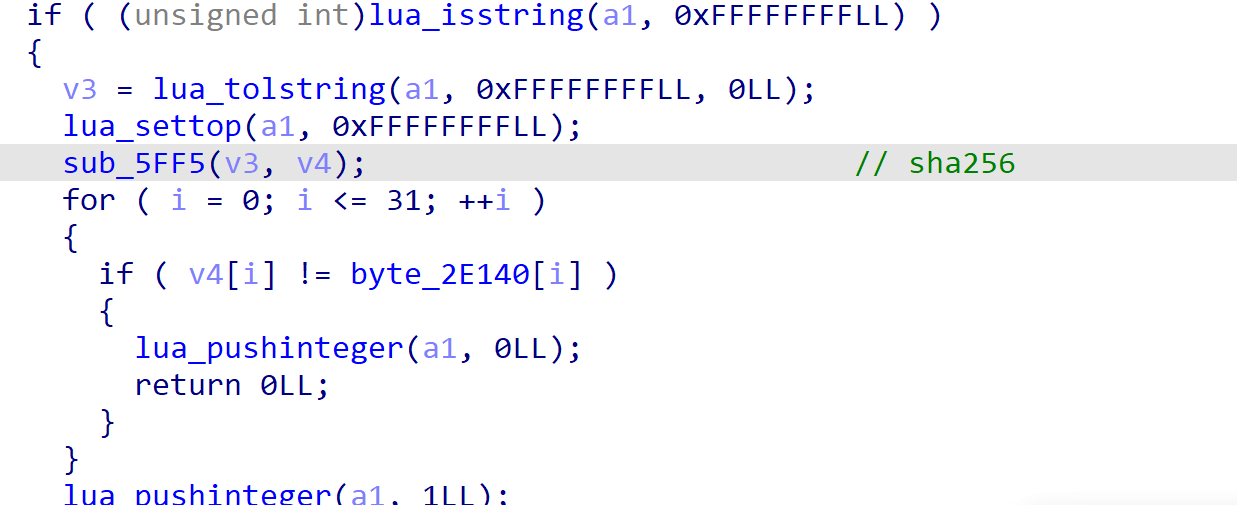
这里,我们直接进行爆破解密即可。
1 | |
程序add存在off-by-null漏洞。
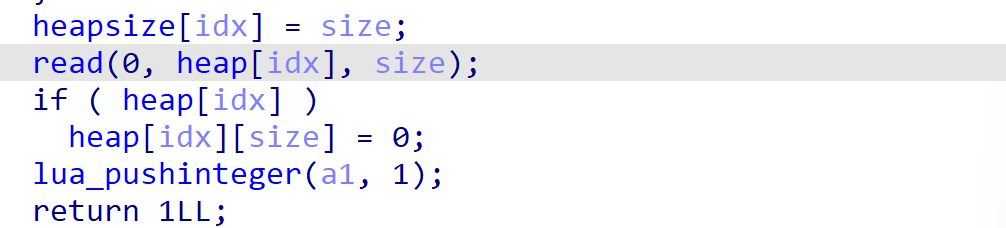
这里我们可以泄露出堆地址,直接伪造fake_chunk通过unlink检查即可,就不需要布置过于复杂的堆风水了。利用直接使用house of cat一把嗦即可。
1 | |
three-boy
检查保护。
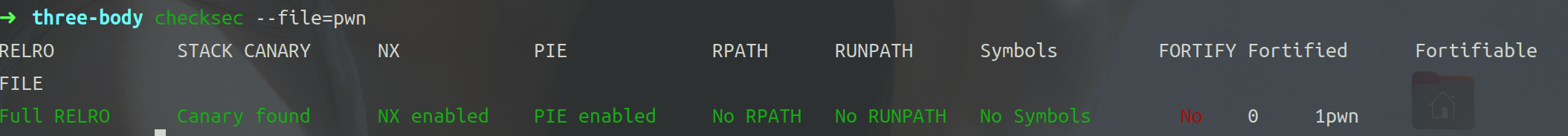
保护全开。
这道题仍然是一道常规的堆菜单题。
sub_17C1函数根据随机数分配堆块。这里为了使我们分配的堆块可控,笔者使用python模拟rand随机数。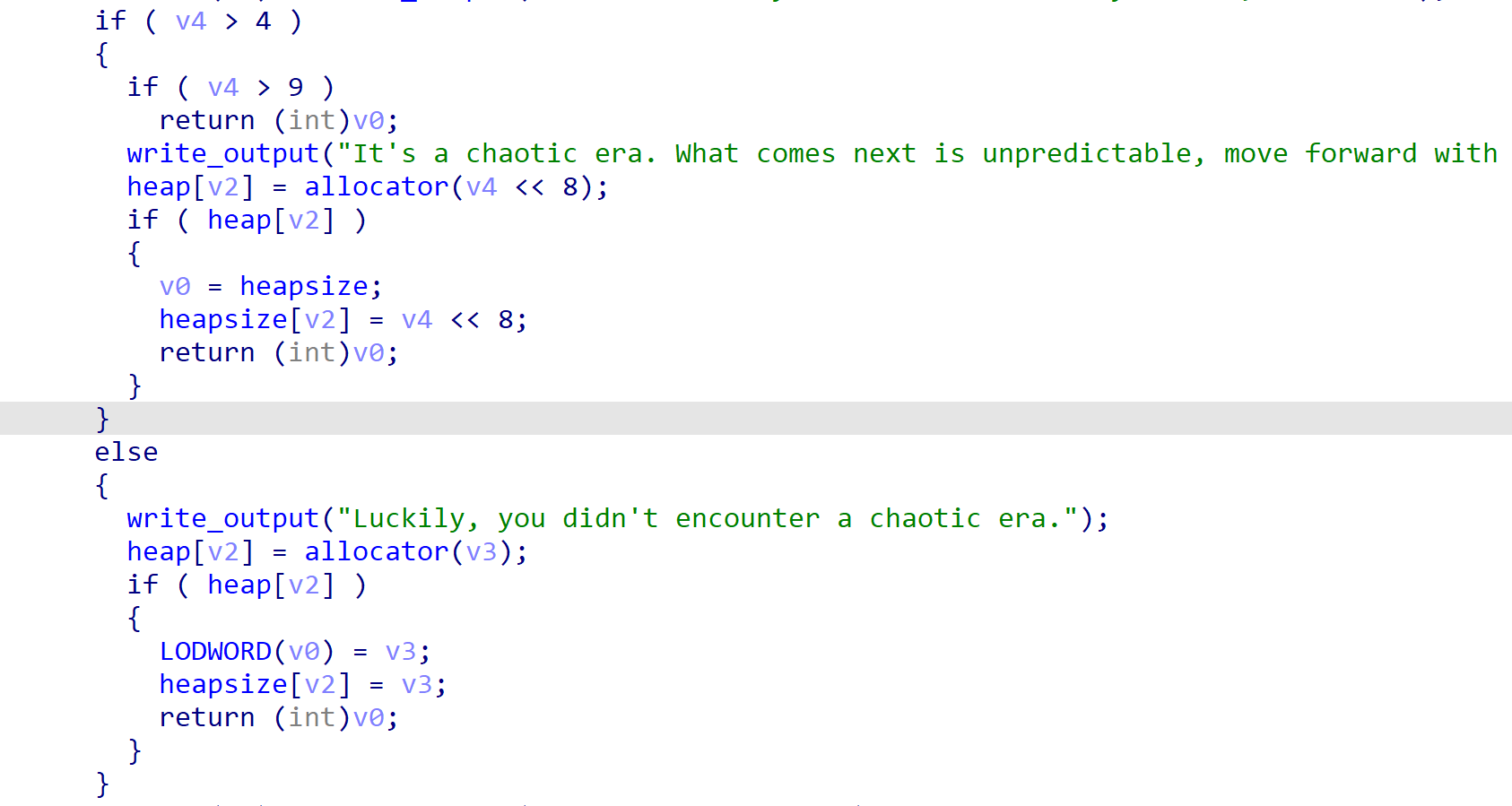
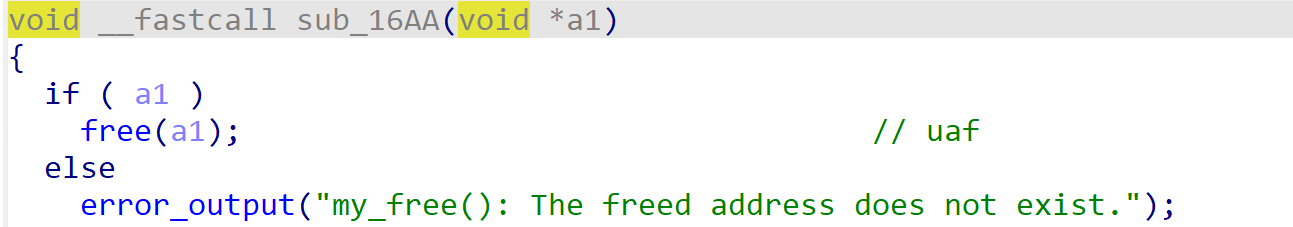
sub_16AA函数存在UAF漏洞。
还可以edit堆块一次以及show堆块一次。
大致思路就是泄露heap以及libc地址,分配比较大的chunk,然后剩下的堆块从这个大的chunk中分割,即可利用一次edit进行largebin attack以及伪造IO file。
笔者这里采用house of obstack的方式获取shell。
1 | |