2023-10月ctf复现记录
2023-10月ctf复现记录
柏鹭杯
eval
程序实现简单的了四则运算(+、-、*、/)。
程序维护的运算结构体大致如下:
1 | |
正常情况下,运算的结果是:num1 += num2。若我们输入非正常的表达式,即以符号作为起始位置,则产生的结果为:count += num1。而程序对数字的索引都是通过count完成的,从而可以实现越界读写。
越界读
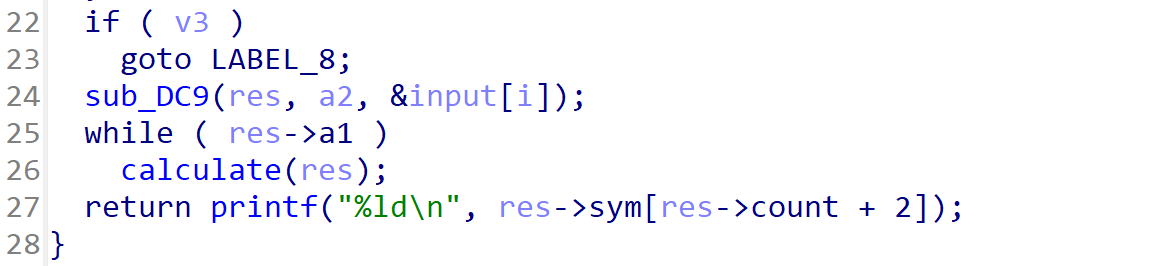
越界写
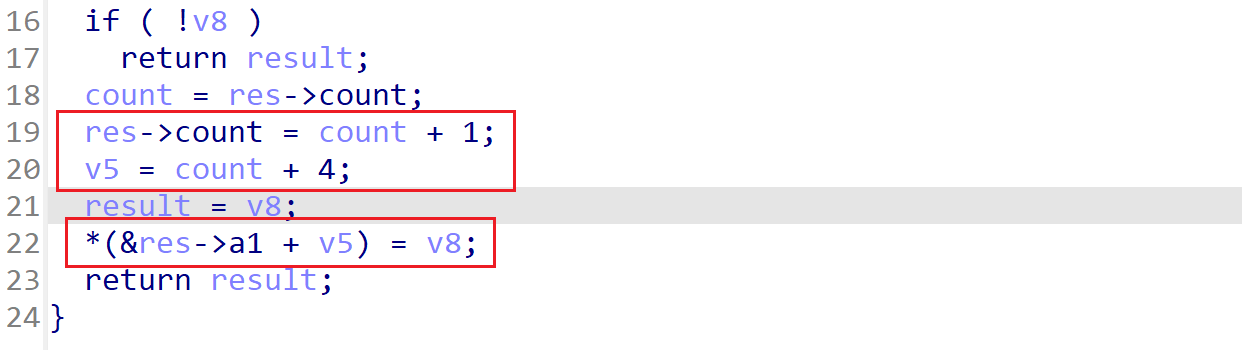
整体思路为:
- 输入畸形表达式实现越界读,泄露libc地址
- 实现越界写,覆盖
sub_E50函数返回地址为one_gadget。
1 | |
heap
程序自定义了堆的分配与释放过程。
程序维护的chunk结构体:
1 | |
自定义malloc
1 | |
自定义free
1 | |
后门函数backdoor
泄露FLAG环境变量。
1 | |
漏洞点
edit功能的任意长度写,造成堆溢出。
1 | |
利用思路
- 分配大于0x80的chunk,释放并泄露libc地址与程序基地址
- 分配小于0x80的chunk,覆盖fastbin的free_fd指针,拿到任意地址xie
- 覆盖malloc_hook为backdoor。
1 | |
香山杯
move
栈迁移到sskd,泄露libc地址,返回到main函数。直接输入system的pop链劫持read返回地址获取shell。
1 | |
pwthon
题目是一个.so文件与main.py文件。
main.py
随机生成文件夹名,然后无限循环执行app库中的函数。app库是由cpython打包而成的.so文件。
1 | |
直接运行main.py文件,报错没有app模块。
根据app.so文件名提示,尝试编译python3.7运行main.py,成功运行。
逆向app.so文件。直接搜索load_arr、calc、app_main等函数,反编译都特别长,一点都看不了。发现前缀都有一个app_,直接搜索,定位到Welcome2Pwnthon 函数。
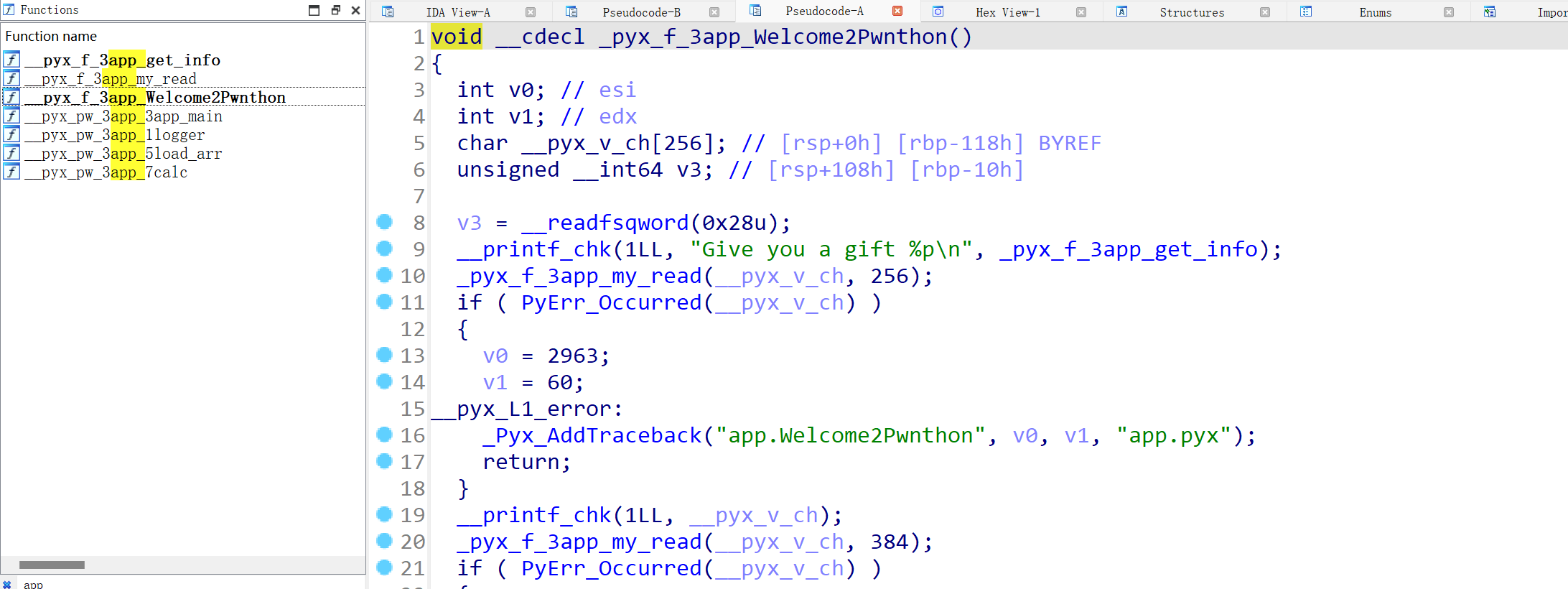
函数直接泄露程序地址,同时发现程序存在格式化字符串漏洞以及栈溢出漏洞。
交叉引用,发现app_main函数调用。
利用思路
- 泄露程序地址
- 通过格式化字符串泄露canary
- 通过栈溢出漏洞泄露libc地址并获取shell
1 | |
DASCTF10月赛
Guestbook
四次操作机会,存在栈溢出漏洞。
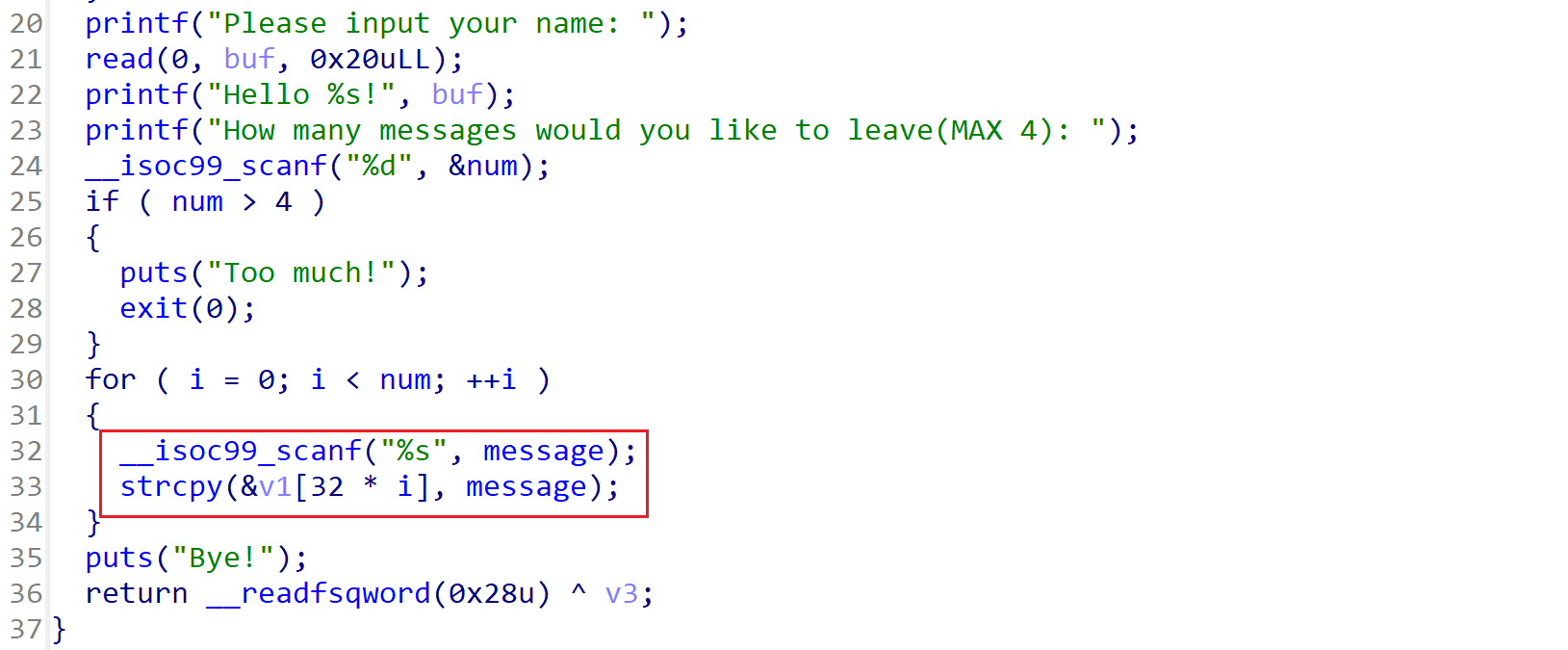
利用思路
- 利用名字打印功能泄露canary
- 利用4次机会覆盖返回地址为backdoor
1 | |
easybox
程序实现了一个简单的shell,实现了cat、ping、ls等简单功能。
pingCommand
check_ip 并没有过滤 ; 与 ` ,存在命令注入漏洞。
1 | |
catCommand
读取文件到栈中,没有检查文件长度,存在栈溢出漏洞。没有过滤 . ,存在目录穿透漏洞。
1 | |
利用思路
- 利用目录穿透漏洞泄露canary
- 利用命令注入向result.txt文件中写入pop链
- 通过catCommand触发pop链
1 | |
binding
使用calloc分配范围0x100~0x200的堆块。
edit
存在栈溢出漏洞,且任意地址覆盖8字节,然后写一字节。
1 | |
show
一次SPECIAL_SHOW机会,泄露任意地址。
1 | |
利用思路
- 堆风水泄露libc地址
- 利用一次special_show泄露heap地址
- 利用一次EDIT_TIME,覆盖canary为0,且栈迁移到堆上
1 | |
BadUdisk
提供了两个二进制程序。
查看Dockerfile,程序首先运行start.sh,然后运行start_damon.sh ,其不断检测mkudisk与vold进程是否存在,且vold进程在mkudisk进程之后运行,最后先运行mkudisk程序,然后运行vold。
反编译两个程序。
可以看到,两个进程间通过posix信号量通信。
mkudisk
1 | |
vold
1 | |
利用思路
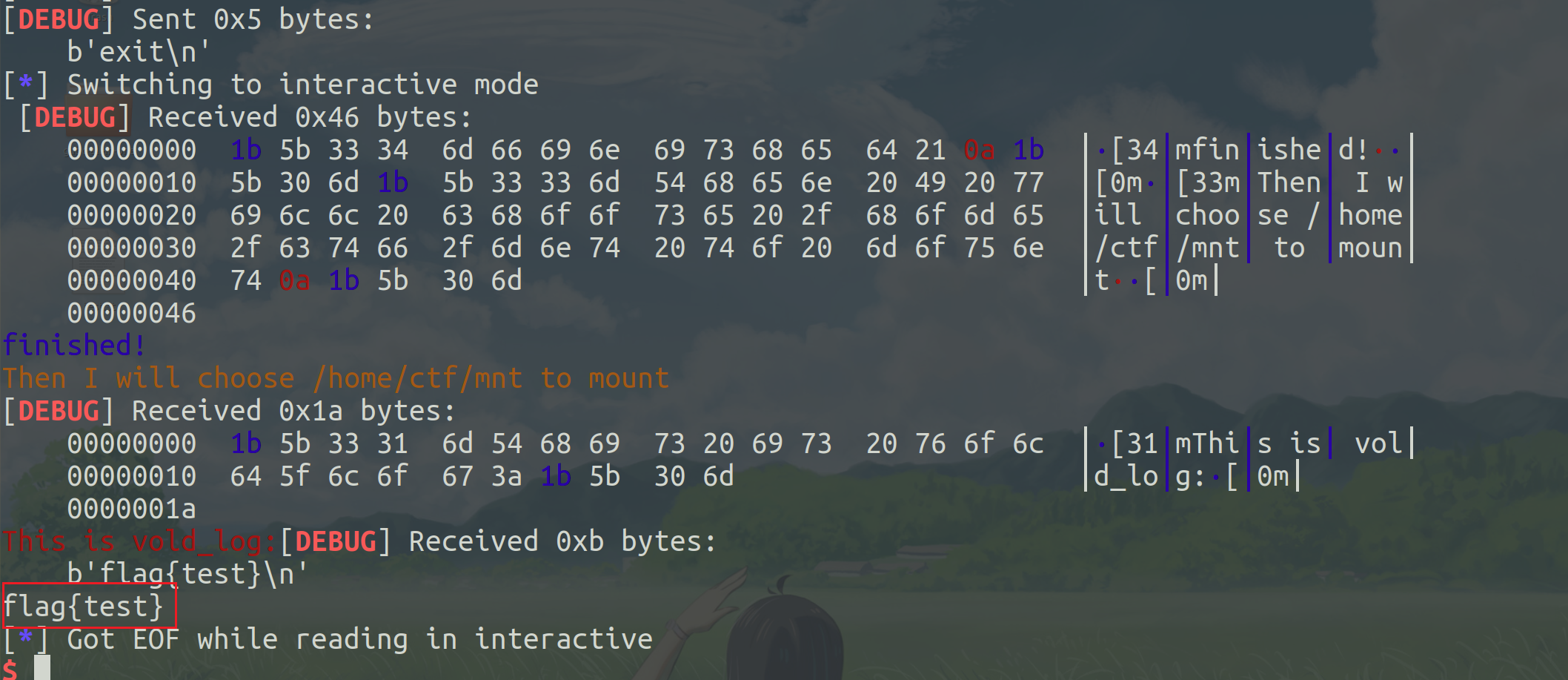
利用mount进行suid提权。
- 在label中写入**../mybin**
- 在 /home/ctf/tmp 中创建log文件并写入修改flag权限的指令
vold最终执行mount时,实现suid提权
1 | |
参考文档
https://blog.xmcve.com/2023/10/13/%E6%9F%8F%E9%B9%AD%E6%9D%AF2023-Writeup/#title-8
https://www.cnblogs.com/ve1kcon/p/17766267.html
https://hkhanbing.github.io/2023/10/17/2023-%E9%A6%99%E5%B1%B1%E6%9D%AFpwn-wp/
https://test-cuycc6s9lprw.feishu.cn/docx/T7budbiSWoTNd4xQGVicHL1Vnpf